How to Use SSH in Linux

If you need to use SSH in Linux to remotely manage other computers, this guide will walk you through doing just that.
In today’s interconnected landscape, the ability to manage computers from different geographical locations has grown from luxury to necessity. There are several ways to do this, depending on the operating system in use. For Linux-based systems, the most common and most secure way to manage your PC remotely is to use SSH (or Secure Shell).
Let’s dig into how to use SSH on Linux to connect to other computers.
Essential First Steps
Before you can successfully connect to another Linux computer with SSH, you’ll need to meet the following prerequisites:
- The target computer must remain powered on and connected to a network.
- The necessary client and server software must be installed and activated.
- You’ll need to know the IP address or hostname of the target machine.
- Appropriate permissions for remote access must be in place.
- Firewall configurations on the remote computer must allow the incoming connection.
If you’re accessing a Linux computer run by, say, your web hosting company, they should have already taken care of all of that. Next, you may have to do some basic software installation on your own Linux computer.
Using SSH On Linux: A Practical Guide
Establishing a functional SSH connection requires both client and server software modules. OpenSSH serves as an open-source alternative predominantly for Linux platforms.
To install the proper OpenSSH client, you’ll need terminal access on your local machine. Note that Ubuntu systems lack a pre-installed SSH server.
Installing an OpenSSH Client
Before delving into the installation process, you should check to make sure the SSH client isn’t already there. To do that, just open a terminal window. You can either search for “terminal” or press ctrl + alt + t on your keyboard.
Once in your terminal window, test for the presence of the SSH client by typing the following:
$ ssh
If the Linux computer has an SSH client already installed, you’ll see the following information scroll across the screen.
usage: ssh [-46AaCfGgKkMNnqsTtVvXxYy] [-B bind_interface] [-b bind_address] [-c cipher_spec] [-D [bind_address:]port] [-E log_file] [-e escape_char] [-F configfile] [-I pkcs11] [-i identity_file] [-J [user@]host[:port]] [-L address] [-l login_name] [-m mac_spec] [-O ctl_cmd] [-o option] [-p port] [-Q query_option] [-R address] [-S ctl_path] [-W host:port] [-w local_tun[:remote_tun]] destination [command [argument ...]]
If, instead, you receive a complaint about the file not being found, you will need to go ahead with OpenSSH client installation. Fortunately, this is simple enough.
On Ubuntu and other Debian-based installations, just run the following command in Terminal:
$ sudo apt install openssh-client
If you’re running Fedora or another distribution that uses yum instead of apt, just run this command:
$ sudo yum -y install openssh-clients
Newer Fedora systems may use dnf instead. If that sounds like you, the magic command is:
$ sudo dnf install -y openssh-clients
Follow the on-screen instructions, and you’ll be good to go in no time.
Initiating an SSH Connection
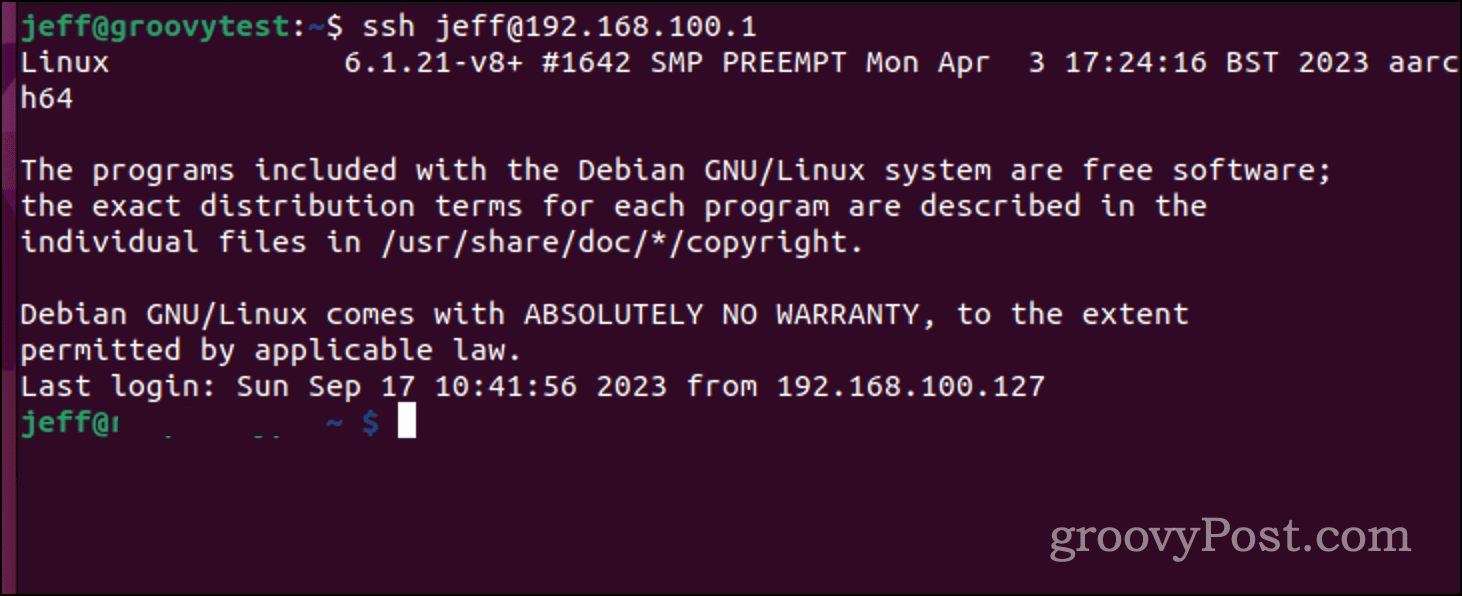
Once you’ve made sure the SSH client is installed on your Linux computer, it’s time to kick off that first connection. While you’re still in the terminal window, issue the following command:
$ ssh username@host_ip_address
If usernames match across local and remote machines, simply enter:
$ ssh host_ip_address
The first time you connect, you’ll be greeted with a prompt asking if you want to continue connecting to the unknown computer. At this point, type yes and continue.
Key in your password, understanding you won’t get any on-screen feedback during entry. Once done, you should be logged into the remote server and can start doing whatever task you need to perform on that computer in the first place.

Understanding SSH: A High-Level Overview
Secure Shell, or SSH — occasionally denoted as Secure Socket Shell — is a protocol enabling secure connectivity to remote servers or computers through a text-based interface.
Upon authenticating a secure SSH channel, a shell session initializes, allowing command-line interaction from your local machine.
This protocol is well-known and loved by system and network administrators, as well as anyone needing secure remote machine management.
Mechanics of SSH Functionality
Establishing an SSH channel mandates the collaboration of two pivotal components: a client-side application and its server-side counterpart. The client application initiates the connection by providing remote host credentials.
If verified, the software creates an encrypted channel between the two computers. On the remote machine, an SSH daemon continually scans a designated TCP/IP port for potential connection requests.
Upon receipt, the daemon conveys its software and protocol capabilities, and both entities swap identification data. An encrypted session ensues if credentials match, predominantly via SSH protocol version 2.
Advanced SSH Usage: Storing Your Encryption Key to Avoid Entering a Password
Now, let’s say you want to avoid having to enter your password each time you log into a remote server. For a secure, password-free connection to another computer, an SSH (Secure Shell) key is indispensable.
You might already possess such a key, but generating a fresh one is never a bad idea. Originating on your local computer, an SSH key is divided into two distinct elements: a confidential, private key — never to be divulged — and its public counterpart. This public key is then disseminated onto any remote systems you need to log into.
Some folks may opt for one SSH key for a multitude of applications, ranging from remote system logins to GitLab. One key to rule them all, you might say. However, my approach is more granular. I use different keys, each designed for a specific subset of tasks.
For example, I utilize a dedicated key for local machines within my home network, another exclusive key for web servers under my administration, and yet another unique key for interacting with Git hosts.
Creating a New SSH Key Pair
Here’s how you can create a new SSH key and then copy it to the remote server you want to use it for. First, create the key using ssh-keygen.
$ ssh-keygen -t ed25519 -f /.ssh/lan
The flag -t specifies the type of key to create, ensuring the encryption is higher than the default. The -f flag sets the key’s file name and location.
When you issue this command, you’ll be prompted to create a password for the key. That password, if you set it, remains local and isn’t sent across the network.
Sending Your SSH Key to the Remote Server
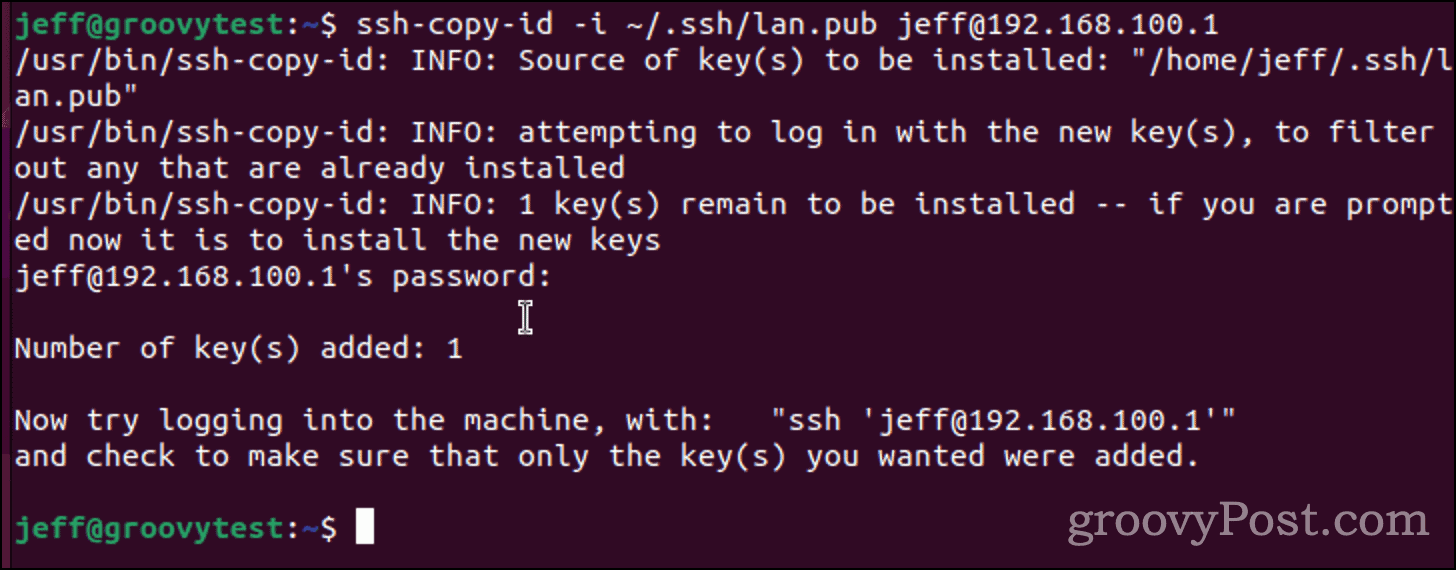
Next, you’ll need to send that security key to the remote server. To accomplish this, just issue this command:
$ ssh-copy-id -i /.ssh/lan.pub user@host_ip_address
You will be prompted for your login password on the remote host. Once the process is complete, though, your key will be installed on that computer.

You should test by trying to log into the remote computer. When you do ssh into the remote host again, you’ll be asked for the passphrase for the key, if you set one. This isn’t your login password, remember. It’s the passphrase specific to that SSH key.
On many distributions, including Linux, this passphrase prompt will open as a dialog box. As you can see from the example below, you can check a box to have the Linux computer remember the passphrase. That will reduce the security of the key, though.

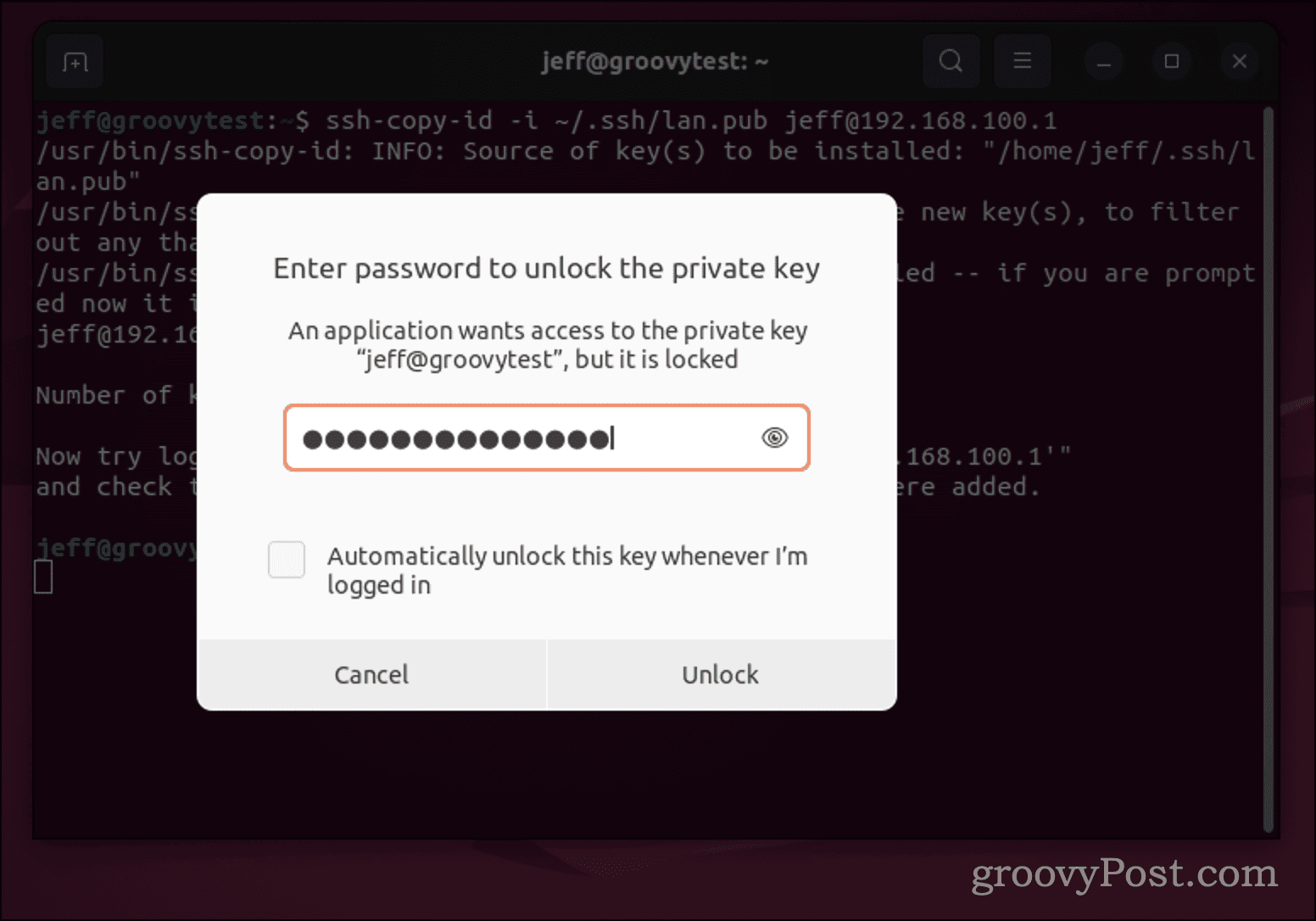
Once you’ve entered the passphrase for your SSH key, you shouldn’t have to type it in again until you log out of the local computer.
Other Ways to Use SSH
With all of that done, you’re good to go to use SSH for remote access to other Linux or Unix-based computers. Of course, it’s not all about getting to the command prompt.
SSH also includes a secure way of transferring files between computers without using FTP. You can use Secure Copy, or scp, to move those files around. If you’re a Windows 11 user and need to use SSH, you’re in luck since the client is preinstalled. You can even generate and use SSH keys in Windows 11.
Leave a Reply
Leave a Reply
